Row Level Security
Audience:
Audience: Administrators Edition: Enterprise
Overview
Administrators can limit which field values a user can access on a row-by-row basis by creating Row Level Security (RLS) profiles.
This restriction applies to Excel outputs, boxes on the chart, the Profile, and all other occurrences of the field within the application.
Note
Note: Row Level Security restrictions can impact the way template rules are applied to records. When configuring Views, ensure that you do not create rules using restricted fields. Otherwise, the View may not appear as expected.
Accessing Row Level Security Profiles
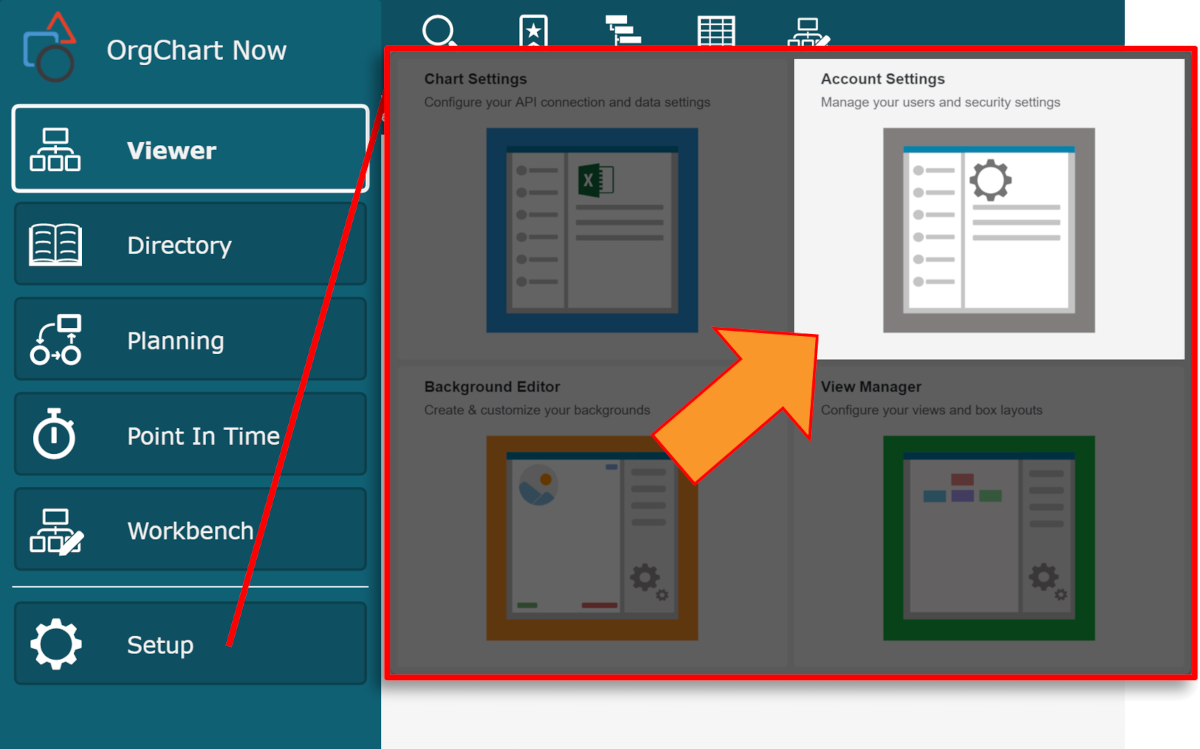
Click on the Mode Switcher icon in the Top Toolbar, and then select the Setup option. The Setup panel is displayed.
Click on the Account Settings tile.
Click on the Security tab in the left side menu.
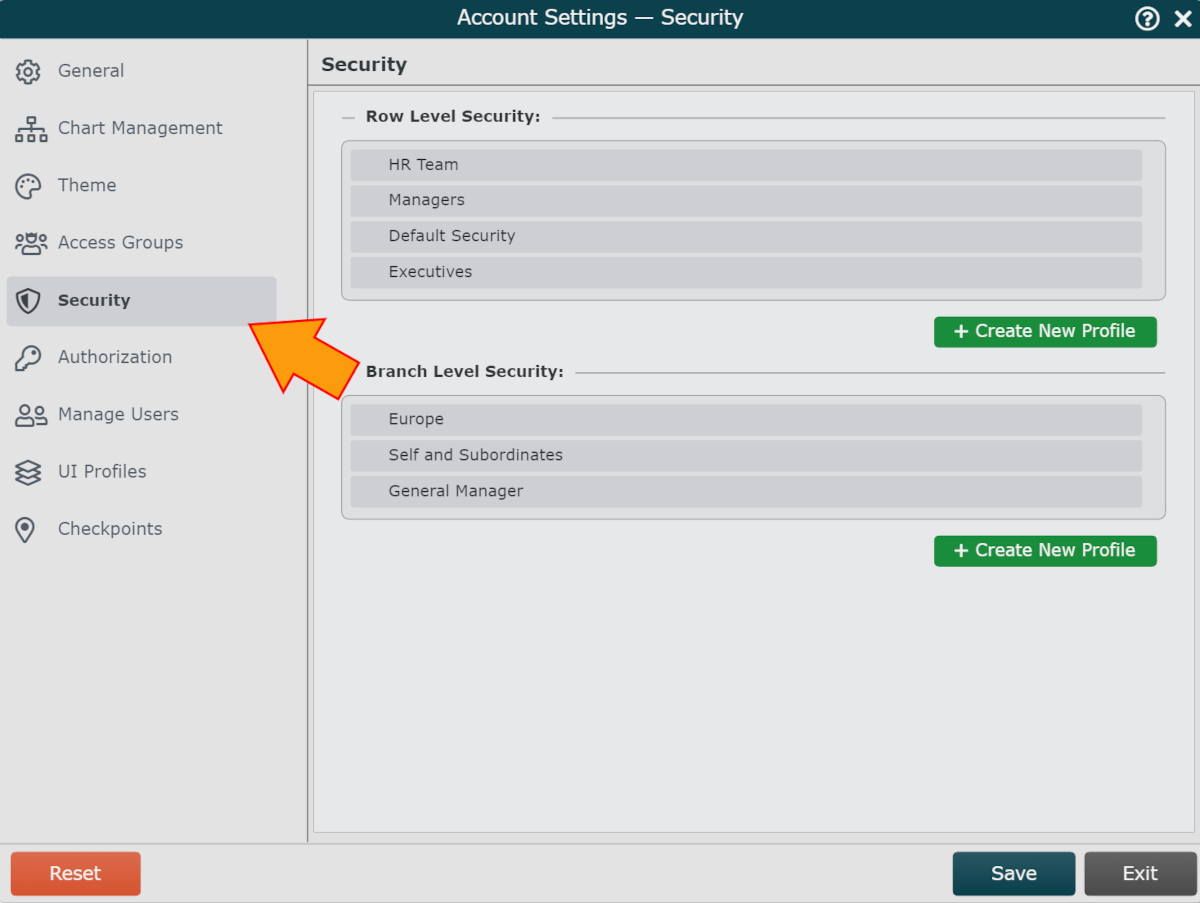
Row Level Security Options
 | Create a new Row Level Security Profile. |
 | Mouse over to configure Row Level Security Profile. See the Security Configuration Options section below for more information. |
 | Mouse over to rename Row Level Security Profile. |
 | Mouse over to copy Row Level Security Profile. |
 | Mouse over to delete Row Level Security Profile |
Tip
OrgChart has pre-installed a Default Row Level Security profile for you to configure.
This Default Row Level Security profile can be modified and renamed, but not deleted.
Mouse over the Default Row Level Security profile, and then click on the  icon to begin constructing the profile. Reference the Security Configuration Options section below for more information.
icon to begin constructing the profile. Reference the Security Configuration Options section below for more information.
Security Configuration Options
In the Security Configuration panel, Administrators can set the conditions under which users assigned to the selected Row Level Security profile are allowed or restricted from viewing specific fields.
Profile Details
Name | Name of the selected Row Level Security profile. |
Description | Description of the permissions set in the selected Row Level Security profile. |
Rule Configuration
Security Rules
Allowed Fields | When selected, only Fields added in the Fields section can be viewed. All other fields are restricted. |
Restricted Fields | When selected, Fields added in the Fields section cannot be viewed. All other fields are allowed. |
 | Add a Conditional Security Rule. Conditional Security Rules allow Administrators to restrict field access for users based on specific Field Value Criteria. Reference the Conditional Row Level Security article for more information. |
Fields
 | Click to add Fields that are either allowed restricted. |
Assigning Row Level Security Profiles
In order to enable Row Level Security for a user, Administrators must assign a Row Level Security Profile to that user's Access Group.
In the Account Settings panel, click on the Access Groups tab in the left side menu.
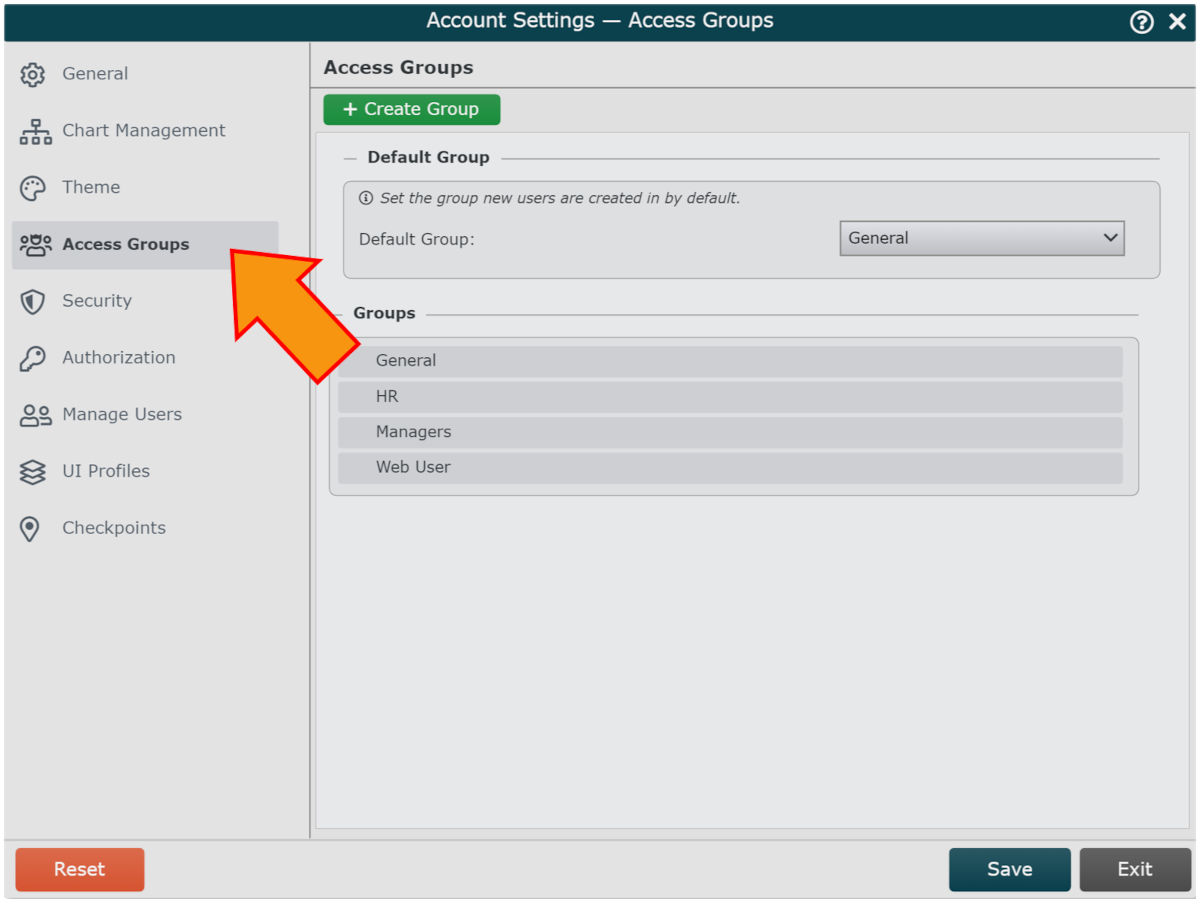
Click on Create Group in the bottom left corner. The following Access Group Configuration panel is displayed:
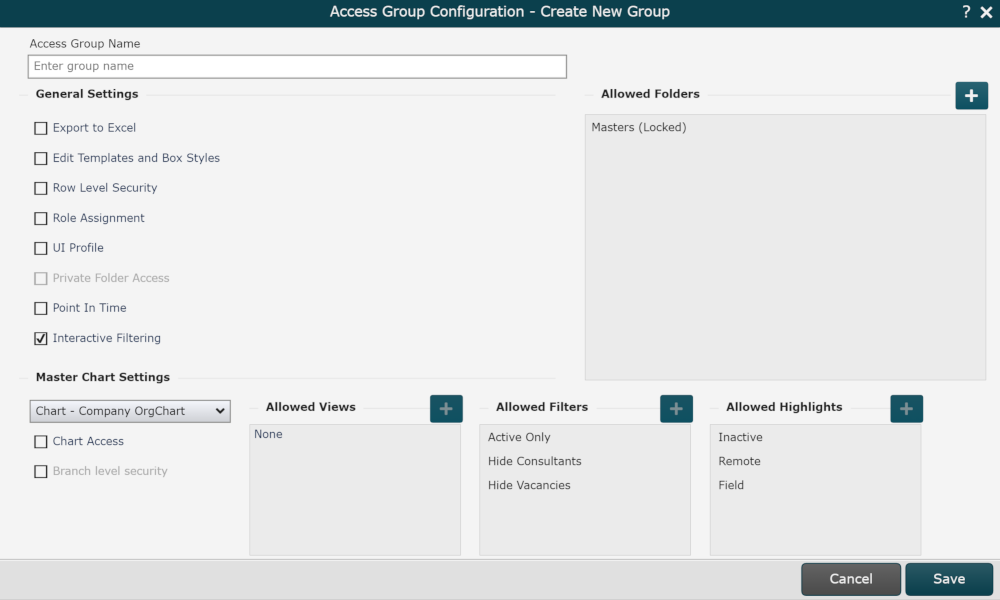
Enter a name in the Access Group Name text box.
Check the Row Level Security checkbox. A dropdown menu is displayed to the right.
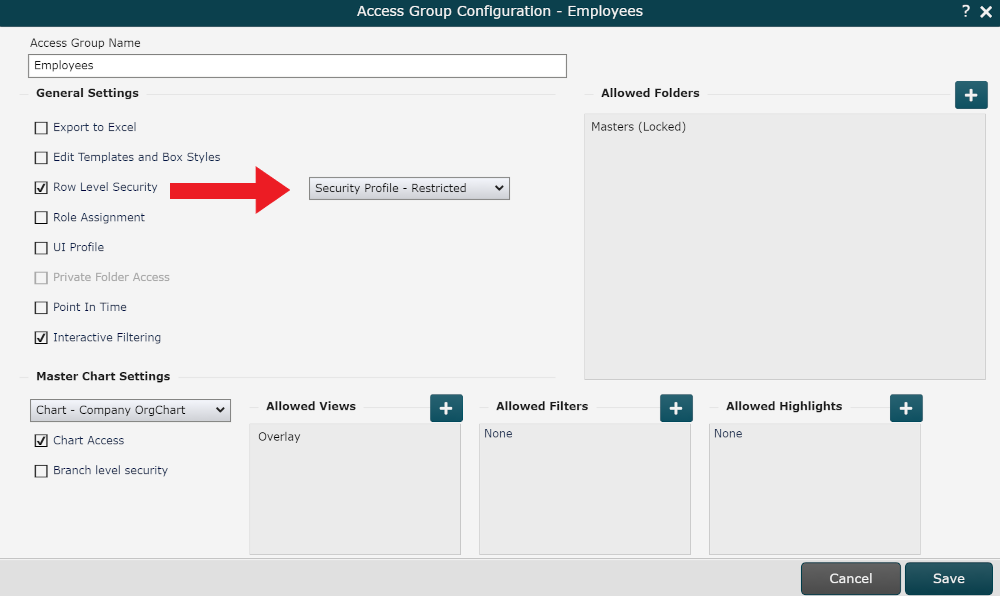
Click on the Row Level Security dropdown menu, and then select the RLS profile you want to assign to this Access Group.
Once you have finished configuring this Access Group, click Save. Reference the Account Settings: Access Group article for more information on configuring Access Groups.
Click on the Settings dropdown, and then select the Manage Users option.
Mouse over the user to whom you'd like to assign the new Access Group , and then click on the
 icon.
icon.Click on the Group dropdown menu, and then select the new Access Group option.
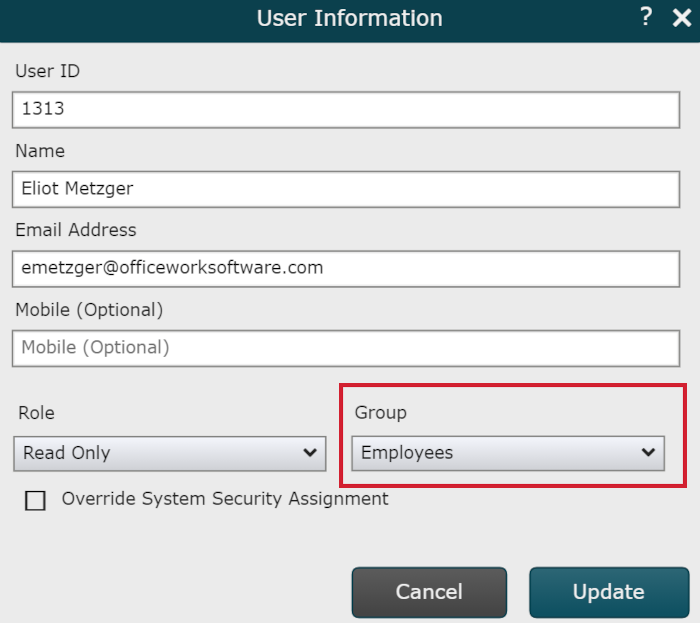
Click Update.
Note
Note: Administrators can impersonate the user to test the permissions. Reference the Admin User Impersonation article for more information.